Discover how penetration testing works and why it’s crucial for keeping your data safe. Due to the bleakness of the cyber threat landscape, penetration testing is now required for a variety of enterprises. You may fully understand pen testing as it relates to websites, systems, and apps after reading this article. The present surge in cybercrime has raised the necessity for penetration testing.
In June 2021, the White House published a document recommending businesses use penetration testing as a ransomware defense. Security professionals must study networks and IT systems from the perspective of nefarious attackers in order to successfully halt, identify, respond to, and recover from cyberattacks. A cybercriminal doing a pen test finds security holes in your network, computer, or programmer and helps you fix them before hackers find and exploit them.
Pen testing consequently becomes a crucial step that no website or business owner may avoid. The benefits of pen testing will be discussed in detail, along with a description of what a penetration tester does. Let’s look more closely at penetration testing and what to expect from it. In this article, we will explore what penetration testing is, and how it works.
What is Penetration testing?
Penetration testing is a cybersecurity practice that aims to identify and exploit vulnerabilities in a system or network to evaluate its security. It involves simulating an attack on a system to find weaknesses that can be exploited by cybercriminals. The purpose of pen testing is to provide organizations with insights into the effectiveness of their security measures and to help them improve their security posture.
What Different Types Of Pen Testing Exist?
Open-box penetration testing – During open-box testing, the attacker will be provided with some background information regarding the subject’s current security measures. When conducting a closed-box pen test, often known as a “single-blind” test, the hacker is only given the name of the desired target company.
When almost no one in the organization is aware that it is happening, such as the IT and intelligence officials who are retaliating to the assault, a covert pen test often referred to as a “double-blind” pen test occurs. Before doing covert testing, it is essential for the hackers to obtain the possibilities and other details in writing in order to avoid any complications with police agencies.
An internal pen test A cybercriminal uses the internal business network to carry out an internal test. This test helps estimate the potential damage a disgruntled employee could cause while operating behind the company’s firewall. An external pen test matches a moral coder against publicly accessible technology the organization uses, including its website and external computer networks.
In such a situation, the hacker was unable even to enter the company’s property. This kind of test enables analysts to gauge the potential damage that a disgruntled employee could cause from within the firewall of the company.
What Happens After a Penetration Test?
Results of penetration tests, which are frequently gathered and evaluated using a report, can be used by organizations to estimate security risks and create action plans. These analyses completely comprehend the hazards associated with a network, enabling organizations to close gaps and strengthen their defenses, especially if a study finds that a system has been compromised.
A penetration testing report must specifically list weaknesses and put them into context in order for the company to minimize its possible dangers. The most useful reports include parts that thoroughly break down individual problems, provide corrective advice, break down the complexity of the evaluation stage, break down design risk, and offer strategic recommendations.
Think of penetration testing as regular checkups. Any organization must routinely evaluate the efficacy of its cybersecurity defenses. With the aid of routine review, your company can adapt to the dynamic threat environment.
What Benefits Do Penetration Tests Provide?
In a perfect world, software and systems would have been built from the ground up to be free of damaging security flaws. Pen testing offers insight into the achievement of that objective. Pen testing can help a business find system weaknesses.
Examine the resistance of the controls.
Encourage adherence to data privacy and security regulations like HIPAA, PCI DSS, and GDPR. Provide management with qualitative and statistical proof of the current security situation and the main financial goals.
CONCLUSION
As part of penetration testing (pen testing), a simulated assault that has been approved is conducted on a computer system to evaluate its security. To find and show the financial impact of a system’s flaws, ethical hackers use the same instruments, tactics, and methods as attackers.
During penetration tests, the vast majority of attacks that could damage an organization are frequently simulated. They may evaluate numerous system functionalities as well as a system’s resistance to attacks from both legitimate and illegitimate sources. Any network area can be examined during a penetration test if the scope is right.
FAQs:
Q: What is the difference between vulnerability scanning and pen testing?
A: Vulnerability scanning involves identifying and reporting on vulnerabilities in a system or network, while penetration testing goes a step further by attempting to exploit those vulnerabilities to test the system’s security defenses.
Q: What are the types of penetration testing?
A: There are several types of penetration testing, including network penetration testing, web application pen testing, mobile application pen testing, and social engineering pen testing.
Q: Who performs penetration testing?
A: Penetration testing is usually performed by a team of skilled cybersecurity professionals who are trained in identifying and exploiting vulnerabilities in a system or network.
Q: Why is pen testing important?
A: Penetration testing is important because it helps organizations identify and address security vulnerabilities before cybercriminals can exploit them. It also helps organizations improve their security posture and comply with regulatory requirements.
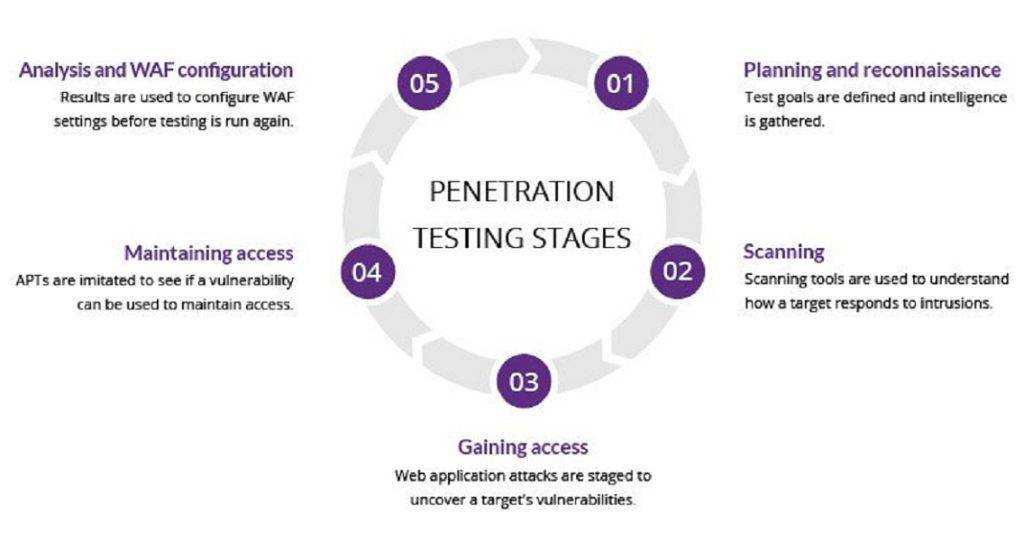
Q: What are the steps involved in a pen testing process?
A: The penetration testing process usually involves the following steps: planning and reconnaissance, scanning, gaining access, maintaining access, and analysis and reporting.


